Worum geht’s?
Vor gut zwei Jahren bekam ich mit, dass die ePaper-Displays, de z.B. in Supermärkten die gedruckten Preisschilder zusehends ablösten, in der Hardware-Hacker- und Maker-Community ‘angekommen’ waren. Damals verhalf mir Aaron Christophel (atc1441), dankenswerterweise zu ein paar “SOLUM GR29000 ePaper Price Tags”, die mit ihrer Diagonale von 2,9″ (~7cm) eine vernüftige “Leinwand” für Experimente boten. Inzwischen sind Preisschilder in ebook-Reader Größe, mit über 5 Zoll, z.B. bei Lidl, ein üblicher Anblick.
So begab es sich also zu der Zeit, dass ich an Weihnachten 2022 einen “ZBS Flasher” aufbaute und ein paar Displays mit der alternativen Firmware für das ePaper Server Project bespielte. Das Projekt nutzte einen ESP8266 oder ESP32 mit einem CC2531 Zigbee-Dongle, um die Displays aus direkter Nähe mit statischen Bildern zu versorgen. Die vergangenen 2 Jahre war so ein Display hier als “Gäste-WLAN Zettel” im Einsatz: unsere Besucher konnten davon die Zugangsdaten ablesen, das Handy mit einem QR Code konfigurieren oder (über ein aufgeklebtes RFID-Tag) per NFC konfigurieren. Das Schöne an den ePaper Displays ist, dass sie keinen Strom benötigen, wenn der Inhalt nur angezeigt, aber nicht verändert werden soll. So lag unser Guest WiFi Tag zwei Jahre “funktionsfähig” ohne Batterien neben dem Telefon…
Auftritt OpenEPaperLink
Bereits ein Jahr später, im Januar 2023, startete Jonas Niesner dann das Projekt OpenEPaperLink (“OEPL”), das eine bessere Verwaltung der Tags erlaubt. Kern der Projekts sind zwei ESP32: der erste (ein ESP-S3 mit PSRAM) übernimmt die Darstellung eines Webfrontends zur Verwaltung der Tags und der zweite (ein ESP32-C6 oder -H2), dient zur Kommunikation mit den Tags über das (modifizierte) Zigbee Protokoll. So ist es nun bequem möglich, mehrere Duzend Displays zu verwalten, und ihnen Funktionen wie eine Google Kalenderanzeige, die Anzeige des Wetters oder eben weiterhin statischer Bilder zu geben.
Da ich wieder etwas Zeit an der Hand hatte, lag es nahe, mein ePaper-Server Setup upzugraden.
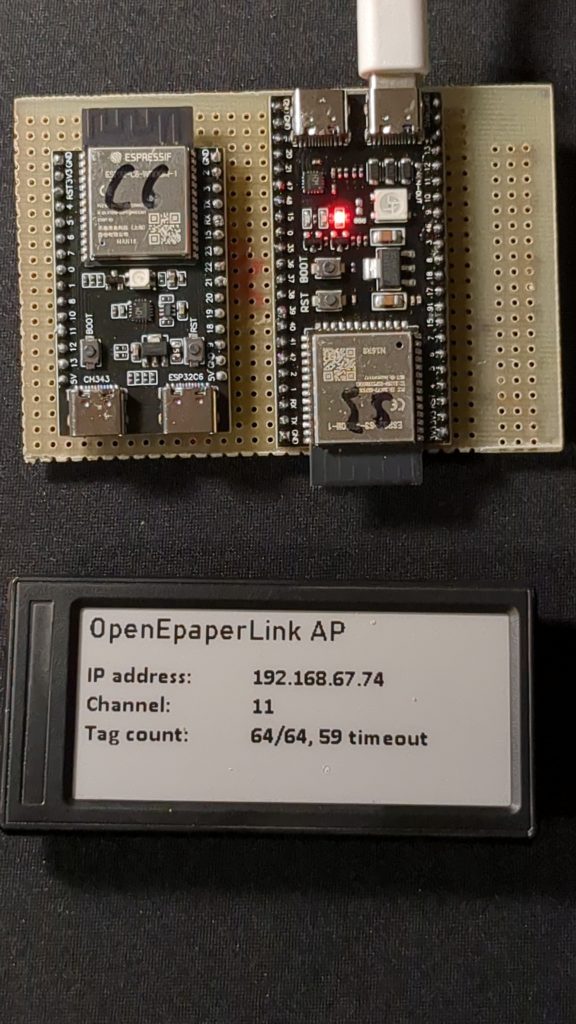
Das OpenEPaperLink Projekt auf GitHub beschreibt in seinem Wiki recht detailiert ein paar Startpunkte für einen OEPL Server. Ich entschied mich für den sog. “Spaghetti-AP”, bei dem die beiden ESP über Dupont Steckkabel miteinander verbunden werden.
Einkaufsliste AP
Der Spaghetti-Server benötigt:
- einen ESP32 mit ausreichend PSRAM, wie einen ESP32-S3 N16R8 (z.B. auf AliExpress oder ebay) für ca. 6-10 €
- einen ESP32 mit Zigbee Protokoll, wie den ESP32-C6 oder -H2 (hier oder dort) für nochmal 6-12 €
- ein USB-C Kabel, um die Microcontroller zu betanken
- ein USB-Netzteil, um den AP ggfs. später unabhängig von einem Rechner zu betreiben
Umsetzung
Das OEPL Wiki beschreibt, wie die beiden ESP32 zusammengesteckt werden. Das kann entweder über Dupont-Kabel oder durch verlöten geschehen. Die Steck-Variante ist für den Beginn zu empfehlen, um zu testen, ob der Aufbau funktoniert. Insbesondere falls die gekauften Boards von den Beschriebenen abweichen, kann man so schnell den einen oder anderen Port umstecken!
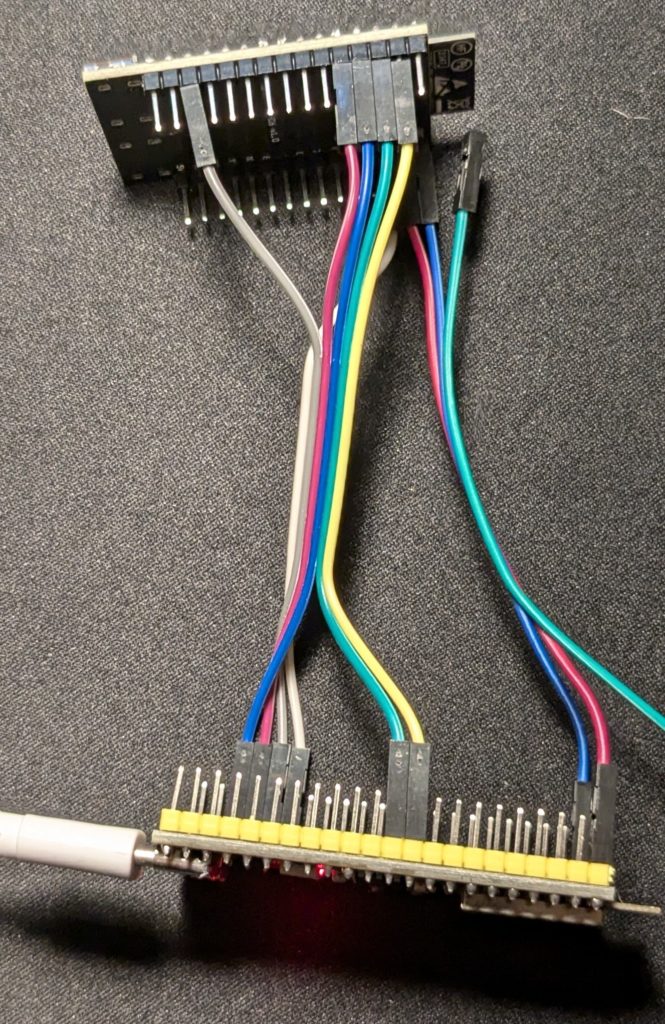
Für einen dauerhaften oder regelmäßigen Betrieb empfiehlt sich die verlötete Variante: Bei meinen 2 Tagen “Dauerbetrieb” mit fliegender Verkabelung, schien es als machte die Steckverbindung das eine oder andere Mal Pause, was nach einem beherzten ‘wackel’ mal am Kabel’ und einem Neustart der ESPs “geheilt” wurde.
sobald die ESP verkabelt sind, werden sie mit der nötigen Firmware geladen. Am bequemsten verrichtet man dies direkt im Browser, mit dem Web-Flasher unter install.openEPaperLink.org. Hier ist darauf zu achten, für den Spaghetti-AP den “Yellow AP” auszuwählen. Die Website funktioniert nur unter Chromium-basierten Browsern (Google Chrome oder MS-Edge). Nachdem der ESP mit dem USB-Port des Computers verbunden ist, gilt es den richtigen COM-Port auszuwählen. Dann wird der erste der beiden ESP32 geflashed. Der Flash-Vorgang benötigt etwa eine Minute. Nach einem Reset des ESP wird der Vorgang mit dem “Yellow AP” wiederholt. Dabei “merkt” der Web-Flasher, dass der erste ESP bereits versorgt ist und bespielt dann den zweiten ESP, der später für die Komunikation mit den Displays genutzt ird, mit einer eigenen Firmware.
Nach einem weiteren Reset kann der OEPL Server dann endlich konfiguriert werden. Dazu spannt der ESP ein eigenes Konfigurations-WLAN (SSID: OpenEpaperLink) auf. Am einfachsten betritt man mit dem Smartphone oder dem Computer das WLAN, und konfiguriert (http://192.168.4.1/setup) initial das eigene Heim-WLAN. So ist der OEPL Server später bequem aus dem LAN erreichbar. Eine feste Adresszuweisung und ein “merkbarer” Name, den man in der Fritz!Box für den AP vergibt, erleichtern auch in ein paar Monaten die Verbindung…
(Nachtrag: zu guter Letzt habe ich dem AP noch ein 3D gedrucktes Gehäuse verpasst.)
Die Displays vorbereiten…
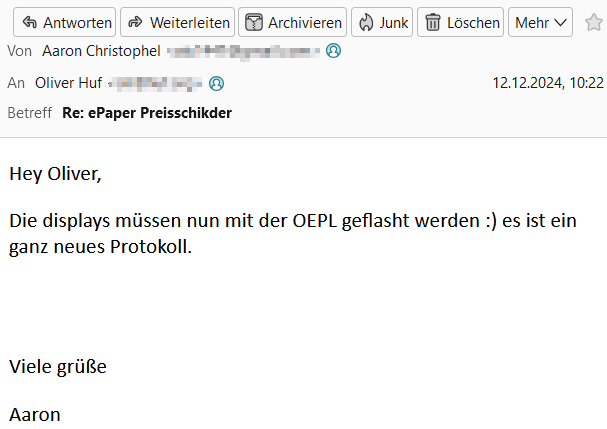
Da ich, wie in der Einleitung beschrieben, vor zwei Jahren bereits ein paar der Displays mit einer alternativen Firmware für den ePaper Server beglückt hatte, hatte ich die Hoffnung, dies nicht nochmals tun zu müssen. Meine Suche führte zu keinem eindeutigen Ergebnis. Zwar beschreibt das OEPL Wiki zwar recht detailliert verschiedene Tags und die nötige Firmware, aber die eigentliche Antwort auf meine konkrete Frage gab erst eine EMail von Aaron Christophel:
… da gehen sie hin, die Hoffnungen auf einen quick-and-dirty Nachmittagshack: mal schnell den AP zusammenstecken und eine Stunde später Erfolg vermelden ;-).
Aber dennoch: Danke, Aaron, für die schnelle Antwort! <3
Einkaufsliste für den Flasher
Um die Tags mit der alternativen Firmware zu betanken, müssen wir nochmals Hand anlegen, da dies nur über die Schnittstelle auf dem Board geht.
Dazu benötigen wir:
- einen “einfachen” ESP32, wie z.B. den ESP32-S2 mini (Ali, Elektrobucht) für ca. 3 Euro
- einen Adapter, um die Preisschilder an den Microcontroller anzubinden.
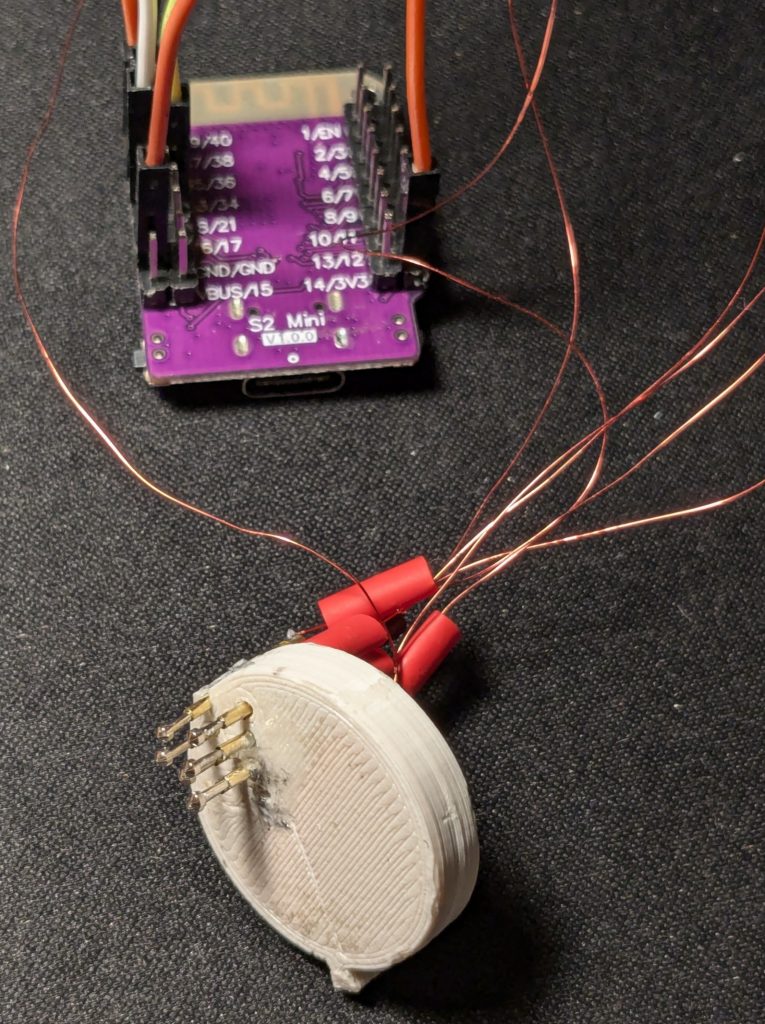
Insbesondere für den Adapter gibt es eine Reihe von Möglichkeiten. Möchte man nur mal 1-2 Displays betanken, kann es ausreichen, die notwendigen 9 Käbelchen direkt auf die Platine des Displays zu löten. spätestens nach dem dritten Display schaut man sich aber nach einer anderen Möglichkeit um. Hier bietet es sich an Federkontaktleisten, sog. “Pogo Pins” zu besorgen, die man z.B. in ein 3D-gedrucktes Element einklebt und mit dem ESP32 verbindet. Damit kann man je nach Modell und Aufwand mehr oder weniger bequem viele Displays in Serie flashen, indem man die Pins auf die Kontakte des Displays drückt:
- Pogo Pins mit 1mm Durchmesser bei AliExpress oder ebay (ruhig ein paar mehr ordern..)
- eine Aufnahme für die Pins. Hier gibt es 3D-Druck Modelle für verschiedene Displaytypen: Hier mein Modell für die SOLUM Tags.
- Die Pins lassen sich m.E. am einfachsten mit Lackdraht verlöten. Etwas Vorsicht ist danach beim Umgang mit dem “Rigg” geboten, damit die Kabel nicht abreissen.
Vor zwei Jahren hatte ich bereits den ZBS-Flasher gebaut. Weil nun OEPL den alten ePaper Server ablösen sollte, habe ich einfach meinen Pogo Pin Adapter “kannibalisiert” und an den S2 mini gelötet. Die ersten Displays waren dann auch irgendwann mit der OEPL Firmware beschrieben.
Für neue Tags ist es wichtig, dass die MAC-Adresse des Tags in einen separaten Speicherbereich, die Infopage, geschrieben wird. der OEPL Flasher bietet hierfür die Option -info an. Ich habe mir für den Flash-Vorgang ein Skript geschrieben das diesen Vorgang automatisiert. Mehr dazu in einem weiteren Artikel.
Nach einem Reboot melden sich die Displays dann mit der Firmware Message und, abhängig davon, ob man daran gedacht hat, ihnen die passende MAC-Adresse mitzugeben, warten sie geduldig auf einen Link zum OEPL Access Point (AP).


Sobald der OEPL AP richtig funktioniert, erscheinen die Tags dort im Interface und können testweise beschrieben werden. Sollte man noch kein passend skaliertes Bild zur Verfügung haben, bietet der OEPL AP die Möglichkeit, eine Reie vordefinierter Automationen zu laden, wie z.B.:
- aktuelles Datum
- aktuelles Wetter am Standort
- Wettervorhersage
- QR-Code
Eigene Inhalte
Das Wiki bietet bereits eine Reihe guter Tipps, wie eigene Bilder am optisch besten auf den Tags erscheinen. Ich plane dazu einen separaten Artikel, in dem ich Beispiele vorstelle, Templates verlinke und einige Schriftarten aufzeige, die für eInk besonders geeignet sind.
Links
- Das Open E-Paper Link Core Project: https://openepaperlink.org/
- OpenEPaper Link auf Github: https://github.com/OpenEPaperLink/OpenEPaperLink
- Das Wiki, mit Informationen zu den APs und Tags: https://github.com/OpenEPaperLink/OpenEPaperLink/wiki
- Die Beschreibung des Spaghetti-AP
- Aaron Christophels (“atc1441”) YouTube Kanal hat eine Reihe von interessanten Videos rund um das Thema, inklusive mehrerer Tutorials: https://www.youtube.com/@atc1441/videos
- Aarons Homepage mit weiteren interessanten Projekten: http://atcnetz.blogspot.com/
- Dmitry Grinbergs Artikel zum ZBS243 Microcontroller und Hacking ePaper Price Tags, die das Thema ins Rollen gebracht haben…